Write a C/JAVA program to implement encryption and decryption using Substitution Cipher(Play-fair cipher) algorithms
Substitution Cipher
HARDWARE AND SOFTWARE REQUIREMENT:
1. Intel based Desktop PC: - RAM of 512 MB
2. Notepad/Notepad ++ editor
3.Turbo C++
3.Turbo C++
Ø Substitution ciphers are probably the most common form of cipher. They work by replacing each letter of the plaintext (and sometimes punctuation marks and spaces) with another letter (or possibly even a random symbol).
Ø A monoalphabetic substitution cipher, also known as a simple substitution cipher, relies on a fixed replacement structure.
Ø That is, the replacement(substitution) is fixed for each letter of the alphabet. Thus, if "b" is encrypted to "S", then every time whenever we encounter the letter "b" in the plaintext, we replace it with the letter "S" in the ciphertext.
Ø A simple example is which each letter is encrypted as the next letter in the alphabet: "online smart trainer " becomes "POMJOF TNBSU USBJOFS".
Ø In general, when performing a simple substitution manually, it is easiest to generate the ciphertext alphabet first, and encrypt by comparing this to the plaintext alphabet. The below table shows how we might choose alphabets
Ø Monoalphabetic substitution cipher is susceptible to cryptanalysis (It is used to crack cryptographic security systems and obtain access to the contents of encrypted messages, even if the cryptographic key is unknown.)
Ø Polyalphabetic Cipher is a substitution cipher in which the cipher alphabet for the plaintext alphabet may be different at different places during the encryption process.
Ø Playfair and Vigenere Cipher are the examples of polyalphabetic ciphers.
PLAY-FAIR CIPHER:
Ø In this technique, pairs of letters are encrypted, instead of single letters as in the case of simple substitution cipher.
Ø In play-fair cipher, initially a key table is created. The key table is a 5×5 matrix of alphabets that acts as the key/basic for encrypting the plaintext.
Ø Each of the 25 alphabets must be unique and one letter of the alphabet (e.g. J) is neglected from the table as we need only 25 alphabets instead of 26. If the plaintext consists of J, then it will be replaced by I.
Ø The sender and the receiver decide on a particular key, say ‘switch.
Ø In a key table, the first of all fill up the cells (going left to right) in the table with the phrase, excluding the duplicate letters. The rest of the cells of table will be filled with the remaining letters of the alphabet, in natural order. The key table works out to be
S
|
W
|
I
|
T
|
C
|
H
|
A
|
B
|
D
|
E
|
F
|
G
|
K
|
L
|
M
|
N
|
O
|
P
|
Q
|
R
|
U
|
V
|
X
|
Y
|
Z
|
STEPS FOR ENCRYPTION:
1) First, a plaintext message is broken into pairs of two letters. If odd number of letters are available, then “Z” is added to the last letter. Suppose we have to encipher/encrypt the message “smart”. It will be written as
SM AR TZ
2) If both the letters are in the same column, take the letter below each one (going back to the top if at the bottom).
3) If both letters are in the same row, take the letter to the right of each one (going back to the left if at the farthest right).
4) If neither of the preceding two rules are true, form a rectangle with the two letters and take the letters on the horizontal opposite corner of the rectangle.
Using these steps, the result of the encryption of ‘smart’ with the key of ‘switch’ would be-
CF EO CY
5) Decrypting the Playfair cipher is as simple as doing the same process in reverse.
SOURCE CODE:
#include<stdio.h>
#include<conio.h>
#include<string.h>
#include<ctype.h>
#define MX 5
void playfair(char ch1,char ch2, char key[MX][MX])
{
int i,j,w,x,y,z;
FILE *out;
if((out=fopen("cipher.txt","a+"))==NULL)
{
printf("File Currupted.");
}
for(i=0;i<MX;i++)
{
for(j=0;j<MX;j++)
{
if(ch1==key[i][j])
{
w=i;
x=j;
}
else if(ch2==key[i][j])
{
y=i;
z=j;
}}}
//printf("%d%d %d%d",w,x,y,z);
if(w==y)
{
x=(x+1)%5;z=(z+1)%5;
printf("%c%c",key[w][x],key[y][z]);
fprintf(out, "%c%c",key[w][x],key[y][z]);
}
else if(x==z)
{w=(w+1)%5;y=(y+1)%5;
printf("%c%c",key[w][x],key[y][z]);
fprintf(out, "%c%c",key[w][x],key[y][z]);
}
else
{
printf("%c%c",key[w][z],key[y][x]);
fprintf(out, "%c%c",key[w][z],key[y][x]);
}
fclose(out);
}
void main()
{
int i,j,k=0,l,m=0,n;
char key[MX][MX],keyminus[25],keystr[10],str[25]={0};
char
alpa[26]={'A','B','C','D','E','F','G','H','I','J','K','L'
,'M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z'}
;
clrscr();
printf("\nEnter key:");
gets(keystr);
printf("\nEnter the plain text:");
gets(str);
n=strlen(keystr);
//convert the characters to uppertext
for (i=0; i<n; i++)
{
if(keystr[i]=='j')keystr[i]='i';
else if(keystr[i]=='J')keystr[i]='I';
keystr[i] = toupper(keystr[i]);
}
//convert all the characters of plaintext to uppertext
for (i=0; i<strlen(str); i++)
{
if(str[i]=='j')str[i]='i';
else if(str[i]=='J')str[i]='I';
str[i] = toupper(str[i]);
}
j=0;
for(i=0;i<26;i++)
{
for(k=0;k<n;k++)
{
if(keystr[k]==alpa[i])
break;
else if(alpa[i]=='J')
break;
}
if(k==n)
{
keyminus[j]=alpa[i];j++;
}
}//construct key keymatrix
k=0;
for(i=0;i<MX;i++)
{
for(j=0;j<MX;j++)
{
if(k<n)
{
key[i][j]=keystr[k];
k++;}
else
{
key[i][j]=keyminus[m];m++;
}
printf("%c ",key[i][j]);
}
printf("\n");
}
printf("\n\nEntered text :%s\nCipher Text :",str);
for(i=0;i<strlen(str);i++)
{
if(str[i]=='J')str[i]='I';
if(str[i+1]=='\0')
playfair(str[i],'X',key);
else
{
if(str[i+1]=='J')str[i+1]='I';
if(str[i]==str[i+1])
playfair(str[i],'X',key);
else
{
playfair(str[i],str[i+1],key);i++;
}}
}
getch();
}
for (i=0; i<strlen(str); i++)
{
if(str[i]=='j')str[i]='i';
else if(str[i]=='J')str[i]='I';
str[i] = toupper(str[i]);
}
j=0;
for(i=0;i<26;i++)
{
for(k=0;k<n;k++)
{
if(keystr[k]==alpa[i])
break;
else if(alpa[i]=='J')
break;
}
if(k==n)
{
keyminus[j]=alpa[i];j++;
}
}//construct key keymatrix
k=0;
for(i=0;i<MX;i++)
{
for(j=0;j<MX;j++)
{
if(k<n)
{
key[i][j]=keystr[k];
k++;}
else
{
key[i][j]=keyminus[m];m++;
}
printf("%c ",key[i][j]);
}
printf("\n");
}
printf("\n\nEntered text :%s\nCipher Text :",str);
for(i=0;i<strlen(str);i++)
{
if(str[i]=='J')str[i]='I';
if(str[i+1]=='\0')
playfair(str[i],'X',key);
else
{
if(str[i+1]=='J')str[i+1]='I';
if(str[i]==str[i+1])
playfair(str[i],'X',key);
else
{
playfair(str[i],str[i+1],key);i++;
}}
}
getch();
}
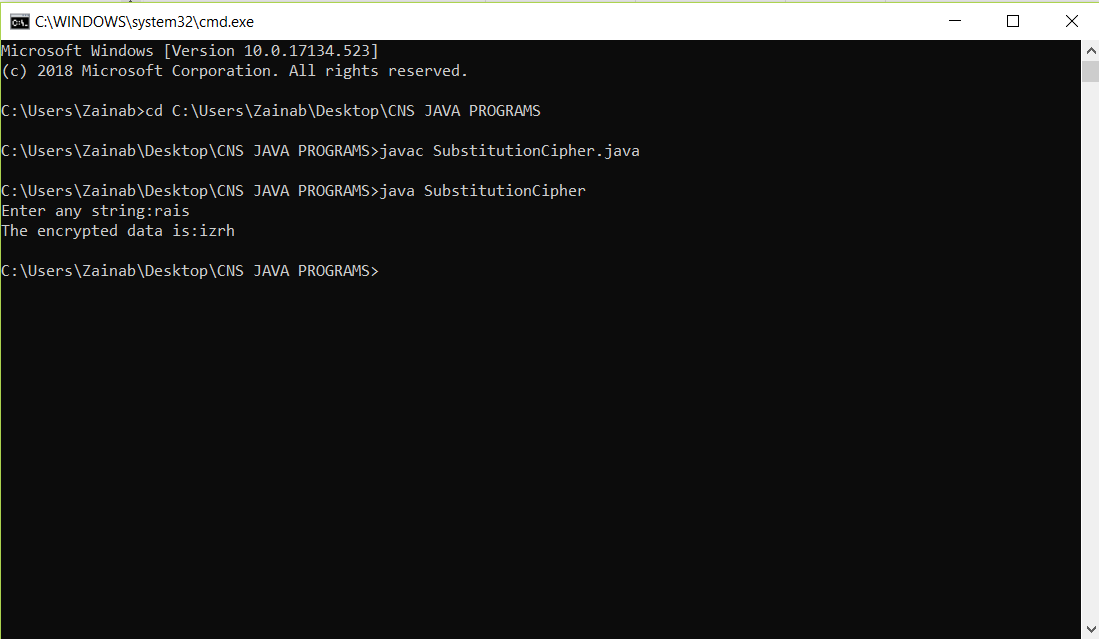
Write a JAVA program to implement encryption and decryption using Substitution Cipher(Play-fair cipher) algorithms
import java.io.*;
import java.util.*;
public class SubstitutionCipher {
static Scanner sc=new Scanner(System.in);
static BufferedReader br=new BufferedReader(new InputStreamReader(System.in));
public static void main(String[]args) throws IOException {
//TODO code application logic here
String a="abcdefghijklmnopqrstuvwxyz";
String b="zyxwvutsrqponmlkjihgfedcba";
System.out.print("Enter any string:");
String str=br.readLine();
String decrypt="";
char c;
for(int i=0;i<str.length();i++)
{
c=str.charAt(i);
int j=a.indexOf(c);
decrypt=decrypt+b.charAt(j);
}
System.out.println("The encrypted data is:"+decrypt);
}
}
OUTPUT:

Comments
Post a Comment