Write a Java program to implement RSA Algoithm | RSA Algorithm in Java | Cryptography
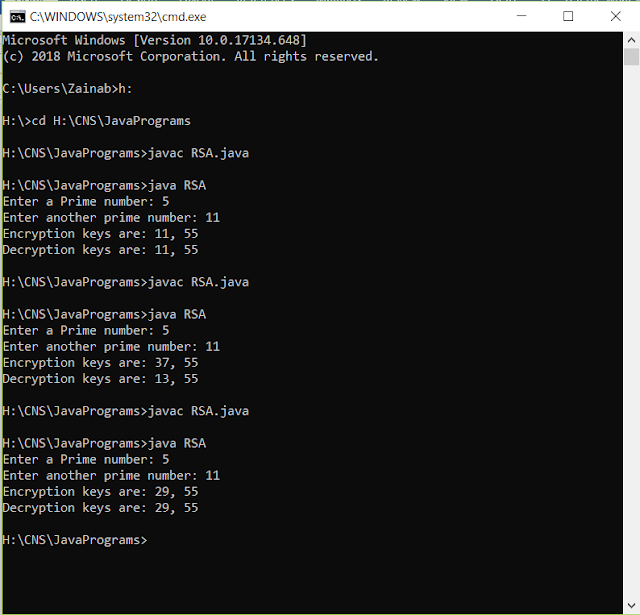
HARDWARE AND SOFTWARE REQUIREMENT: 1. Intel based Desktop PC: - RAM of 512 MB 2. Notepad/Notepad ++ editor and Command Prompt or 3. IntelliJ IDEA Community Edition/ Eclipse THEORY: Ø RSA is an encryption algorithm, in order to have secure transmission of messages over the internet. Ø Many protocols like Secure Shell , S/MIME , and SSL / TLS are based on RSA for encryption and digital signature functions. Ø It is an asymmetric encryption technique [Asymmetric means that there are two different keys i.e. Public key and Private key. That’s why it is also known as public key cryptography]. Ø The public key is used to encrypt messages and can be known to everyone; Messages encrypted using the public key can only be decrypted with the private key / Secret key. An example of asymmetric cryptography in Client-Server Communication: 1. A client (web browser) sends its shared key to the web server and requests for some data. 2. Th
